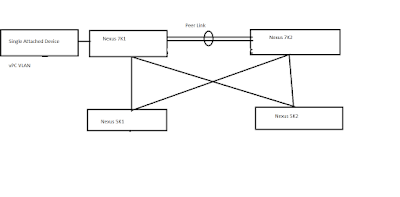
--> vPC is a virtualization technology that allows two Cisco Nexus 7000 or 5000 Series as a Single Virtual node to downstream devices.
--> The Downstream device can be a switch, server, or any other networking device which supports link aggregation technology.
--> vPC architecture contains the following components:
1) vPC Member--> This is also called as vPC Peer device.
--> It can be a Nexus 5000 or Nexus 7000 Series Switch.
2) vPC Domain--> vPC Domain contains two vPC Peer devices.
--> Only 2 peer devices max can be part of same vPC domain.
--> The domain ID must be the same on both peer devices.
--> vPC domain identifiers must be different on both layers because this information is used as part of the LACP protocol.
3) vPC member Port--> This is one of the port which forms vPC.
--> This Port is connected to both of the Nexus 5000/7000 Upstream switches.
4) Orphan Port--> A port that belongs to a single attached device.
--> A port on vPC peer device (primary or secondary) that is connected to a single attached device.
--> A port on vPC peer device (primary or secondary) that carries vPC VLAN.
--> If the port carries a non-vPC VLAN, it is no more defined as Orphan Port.
--> When connecting a single-attached access device to vPC domain using vPC VLAN, always connect it to vPC primary peer device.
--> Reason is when vPC peer-link fails down, any single attached device connected to secondary peer device (and using vPC VLAN) will become completely isolated with the rest of the network.
5) vPC peer-link --> This Link used to synchronize the state between vPC peer devices.
--> It must be a 10-Gigabit Ethernet link.
--> vPC peer-link is an L2 trunk carrying vPC VLAN.
--> Cisco Fabric Service protocol is used for synchronizing the state information between vPC Peers.
--> vPC Peer-link can be formed only with the Same family of modules ( F3-F3 and M3-M3).
6) vPC peer-keepalive link --> The keepalive link between vPC peer devices; this link is used to monitor the liveness of the peer device.
--> It is recommended to use 1Gbps link for vPC Peer-keepalive link.
--> vPC Peer-Keepalive link must be configured before configuring vPC Peer-link.
--> vPC Peer-Keepalive link uses UDP port number 3200 to check reachability between vPC peers.
--> It is recommended to use separate VLAN interface in different VRF for the peer-keepalive link.
--> vPC Peer-Keepalive just requires reachability ( Both VPC Peers can use different Subnet IP Address for Peer-Keepalive).
--> vPC Peer-Keepalive use management VRF by default for checking the reachability between them.
7) vPC VLAN --> VLAN carried over the vPC peer-link and used to communicate via vPC with a third device.
--> vPC VLAN is simply VLAN which is allowed on the peer-link.
8) non-vPC VLAN--> non-vPC VLAN A VLAN that is not part of any vPC and not present on vPC peer-link.
9) Cisco Fabric Services (CFS)--> CFS is the protocol used between vPC peers to share and synchronize the state between vPC peer devices.
--> Cisco Fabric Services (CFS) protocol performs the following functions:
? Configuration validation and comparison (consistency check)
? Synchronization of MAC addresses for vPC member ports
? vPC member port status advertisement
? Spanning Tree Protocol management
? Synchronization of HSRP and IGMP snooping
--> Cisco Fabric Services is enabled by default when vPC feature is turned on.
--> There is no specific Cisco Fabric Services configuration to implement.
10) vPC System-Mac and vPC Local System-Mac--> Once vPC domain is configured both the vPC peers will be assigned with the same MAC address known as vPC System-MAC.
--> vPC system-mac = 00:23:04:ee:be:<vpc domain-id in hexadecimal>
--> It is possible to configure manually vPC system-mac value with the command system-mac inside vPC domain configuration.
--> vPC local system mac is owned by each peer devices so it is unique per device. vPC local system mac is derived from the system or VDC mac address.
--> vPC system-mac is used only with vPC attached access devices while vPC local system-mac is used with single attached devices.
Ref: Cisco.com
Md.Kareemoddin
CCIE # 54759